aCtive sEcurity foR connecTed devIces liFecYcles (CERTIFY)

We are delighted to announce that CERTIFY project has been selected for funding under European Union’s Horizon CL3 Increased Cybersecurity 2021 and Swiss State Secretariat for Education, Research and Innovation (SERI). It is a multi-partner project which aims to provide Internet of Things (IoT) security lifecycle management. CERTIFY will detect and respond to a wide spectrum of attacks, in a collaborative/decentralized fashion. It is 36 months long project. We had the project kickoff meeting on 20 to 21 October 2022 in University of Murcia, Spain.
Partners
It is a consortium project which includes 6 SMEs, 4 industrial partners, 2 universities, and 1 research institute from 8 various countries in Europe.
| SN | Partner Name | Country |
| 1 | Universidad De Murcia | Spain |
| 2 | Trust Up | Italy |
| 3 | STMicroelectronics SRL | Italy |
| 4 | Engineering – Ingegneria Informatica SPA | Italy |
| 5 | Digital Worx GmbH | Germany |
| 6 | United Technologies Research Centreireland Limited | Ireland |
| 7 | Advanced Laboratory on Embedded Systems SRL | Italy |
| 8 | Red Alert Labs | France |
| 9 | The Ubiquitous Technologies Company | Greece |
| 10 | AIR Institute – Deep tech lab | Spain |
| 11 | European Cyber Security Organisation | Belgium |
| 12 | Universität Zürich | Switzerland |
| 13 | modum.io AG | Switzerland |
Objectives
The CERTIFY project has following objectives
- Cybersecurity awareness for IoT-enabled environments through a multi-stakeholder sharing of threats and mitigations
- Secure reconfiguration and maintenance of customizable embedded devices by means of open hardware primitives and services
- Perform security operational management based on bootstrapping and monitoring of attacks and malicious behaviours
- Runtime security compliance and continuous certification methodology via objective metrics
- Foster knowledge delivery via wide dissemination, capacity building and supporting standardization activities. Build a robust exploitation plan to boost ROI by optimizing current and future EU cybersecurity capabilities
- Industrial validation of the CERTIFY framework in IoT ecosystems
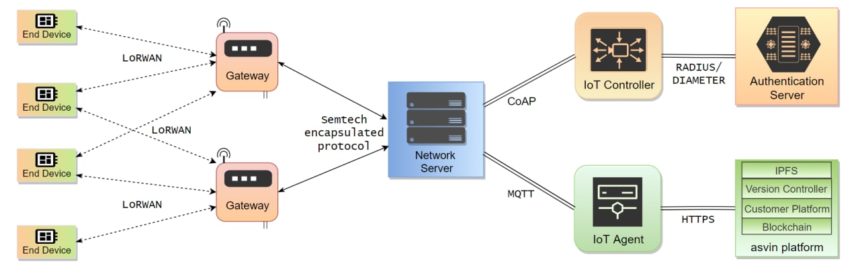
Our Contribution
The project has been structured in 7 work packages (WP) and 3 pilots. Each work package clearly defined objective, tasks, and deliverables. Each project partner will contribute in various tasks. Digital Worx is involved in all work packages. We are the leader of WP6 which focuses on community engagement and sustainability. Additionally, we are leader of task T2.3 Testing, Refinement and Validation and Pilot 2 Smart Micro-Factories. In the pilot, we will install and configure retrofitting sensors in an industrial setting, perform risk assessment, and secure them through their life cycle. In the task 2.3, we will identify validation scenarios and acceptance criteria based on pilot assessment. It will be utilized to validate the technical components and their integration to deliver high quality software. Moreover, digital worx will contribute in developing and deploying secure IoT environments, IoT device inventory, lifecycle support, secure bootstrapping and intrusion detection solution.